Citrix Workspace app for Mac: Conditional Access with Entra ID, based on device compliance
How to support Microsoft Entra ID conditional access, based on device compliance with the native Citrix Workspace app for Mac? While working out of the box with the Citrix Workspace app for Windows, the counterpart for macOS requires adjustments to leverage the system default browser for proper devi
How to support Microsoft Entra ID conditional access, based on device compliance with the native Citrix Workspace app for Mac? While working out of the box with the Citrix Workspace app for Windows, the counterpart for macOS requires adjustments to leverage the system default browser for proper device compliance evaluation, ensuring accurate authentication workflows.
If you are using Microsoft Entra ID (formerly known as Azure Active Directory) as the Identity Provider (IdP) to authenticate Citrix users, you can make use of Conditional Access policies during the authentication flow. For example, it’s possible to tailor the authentication depending on the compliance state of the end user’s device used to connect to a Citrix session.
In our example we want the users to satisfy MFA (multifactor authentication) if they are connecting from a non-compliant endpoint, based on the compliance status in Intune. On the other hand, users connecting from a compliant device, should be allowed to start the Citrix session without the need of MFA.
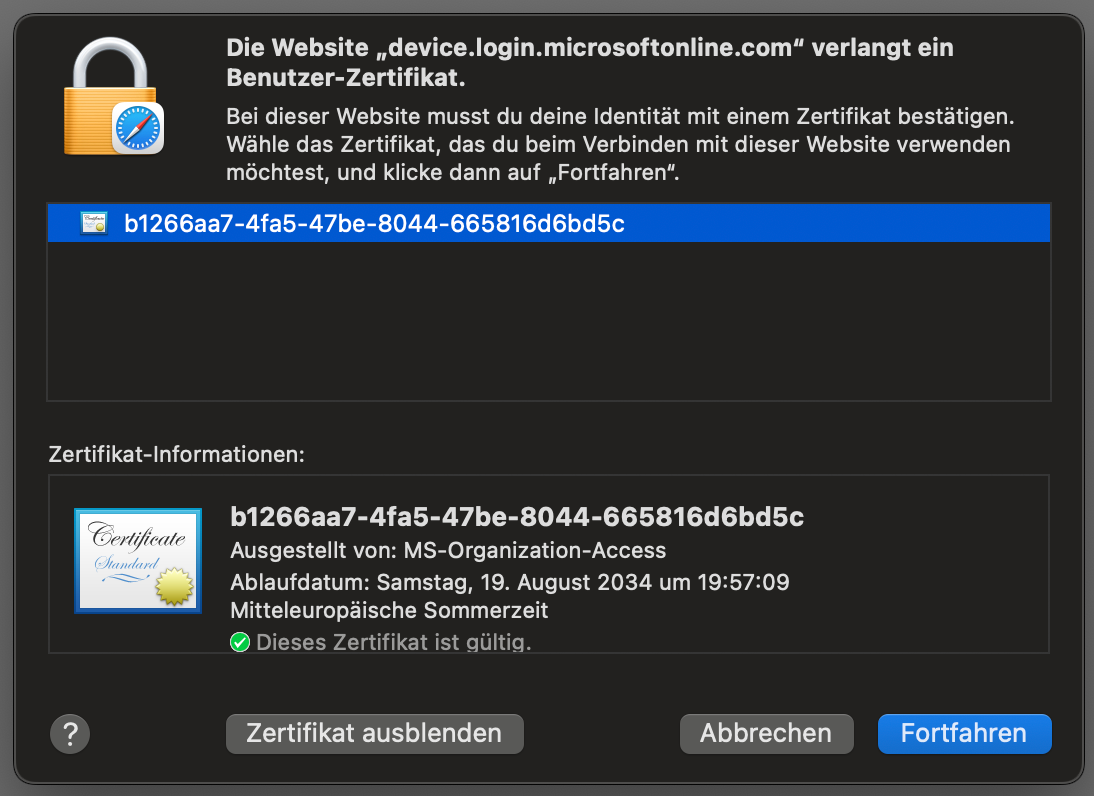
To track the compliance state of a device it must be Microsoft Entra registered or Entra joined, and it must be enrolled into Intune. Based on the configured compliance policies Intune marks the device as compliant or non-compliant. During the authentication against Entra ID the user enters his credentials (username and password in a basic setup) and presents a device certificate, issued by Intune when the device was enrolled into Intune. Based on this device certificate Entra ID know from which device the login is coming and its compliance state (compliant or non-compliant). Depending on this compliance state, Entra ID requests an additional authentication factor (if the device is non-compliant) or just authenticates the user based on the already provided username and password credentials (if the device is compliant).
With browsers like Chrome, Edge, Safari this works out of the box on Windows as well as on macOS devices for Citrix access going through the webstore (browser-based access method). With Citrix Workspace for Windows the same is true for authentications and session launches through the native Workspace app.
Unfortunately, this doesn’t work when using the native Citrix Workspace app for Mac. The Citrix Workspace app for Mac doesn’t have access to the required device certificate and therefore the users always get prompted for MFA because Entra ID doesn’t know from which device the authentication is coming and can’t determine the compliance state of the device.
To make this work, we need to tell the Citrix Workspace app for Mac not to use its internal browser engine for authentication but leverage the systems default browser for the authentication workflow, which has access to the required device certificate needed for device identification and compliance evaluation.
There are several methods to configure the Citrix Workspace app for Mac for this:
- By command line on the device itself
- Through Citrix Global App Configuration Service (GACS)
- Some sort of MDM solutions
To configure a device through command line, open a terminal windows on the macOS device and type the following command:
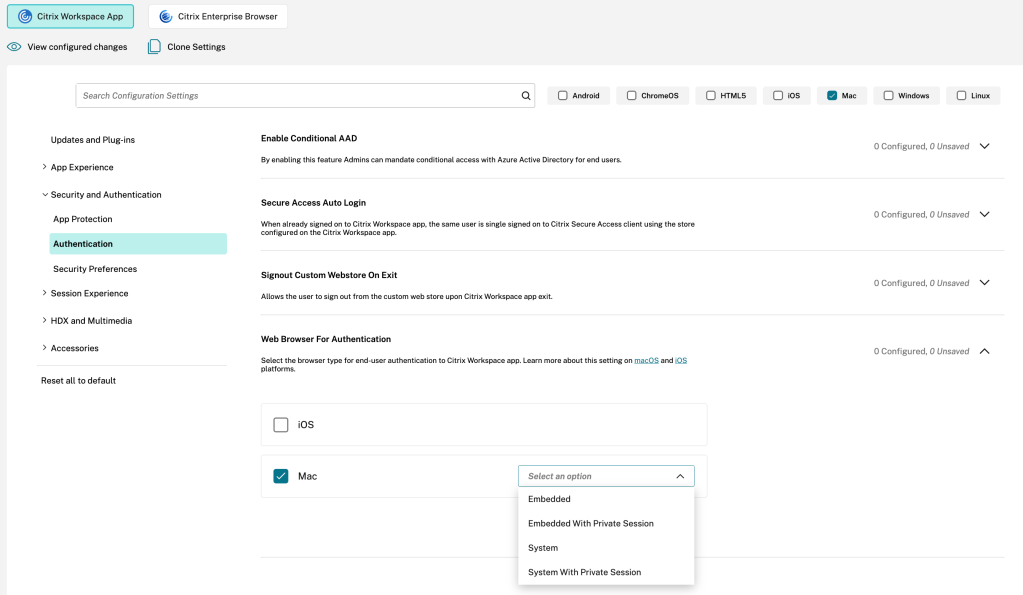
defaults write com.citrix.receiver.nomas WebBrowserForAuthentication SystemTo enable the system default browser for authentication through MDM, administrators must use the following setting:
<key>WebBrowserForAuthentication</key><string>System</string>To use GACS (Global App Configuration Service) to set the system default browser for authentication, administrators must use the following setting:
{
"serviceURL": {
"url": "https://serviceURL:443"
},
"settings": {
"name": "Web browser for Authenticating into Citrix Workspace",
"description": "Allows admin to select the type of browser used for authenticating an end user into Citrix Workspace app",
"useForAppConfig": true,
"appSettings": {
"macos": [
{
"assignedTo": [
"AllUsersNoAuthentication"
],
"category": "authentication",
"settings": [
{
"name": "web browser for authentication",
"value": "SystemWithPrivateSession"
}
],
"userOverride": false
}
]
}
}
}The setting is available in the GUI for Global App Configuration Service as well. Just go to your Citrix Cloud management console, open Workspace Configuration node and choose the App Configuration section. You will find the relevant setting for Mac under Security and Authentication > Authentication. It’s called “Web Browser for Authentication”. Select the option System for Mac.