Multi-factor Authentication for Citrix XenDesktop / NetScaler against Azure AD
In my last post about secure access to XenDesktop virtual workspaces I tried to give an overview of the different ways to implement multi-factor authentication with Citrix NetScaler and XenDesktop. I came to the conclusion that integrating the remote access with Azure AD and using the Microsoft MFA
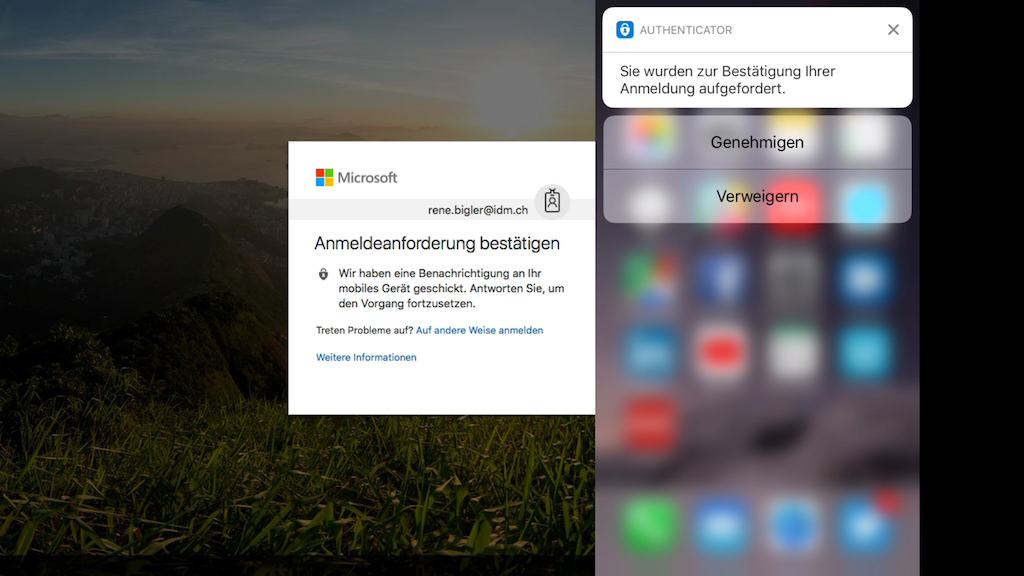
In my last post about secure access to XenDesktop virtual workspaces I tried to give an overview of the different ways to implement multi-factor authentication with Citrix NetScaler and XenDesktop. I came to the conclusion that integrating the remote access with Azure AD and using the Microsoft MFA feature is a very end user friendly way to accomplish this goal, especially when you already have Azure AD in your setup. In this post I will outline a walkthrough to the setup and configuration steps needed.
Settings and Configuration in Microsoft Azure AD
In a first step we need to create a new enterprise application in Azure Active Directory.
- Log in to your Azure management portal (portal.azure.com) and go to the Azure Active Directory
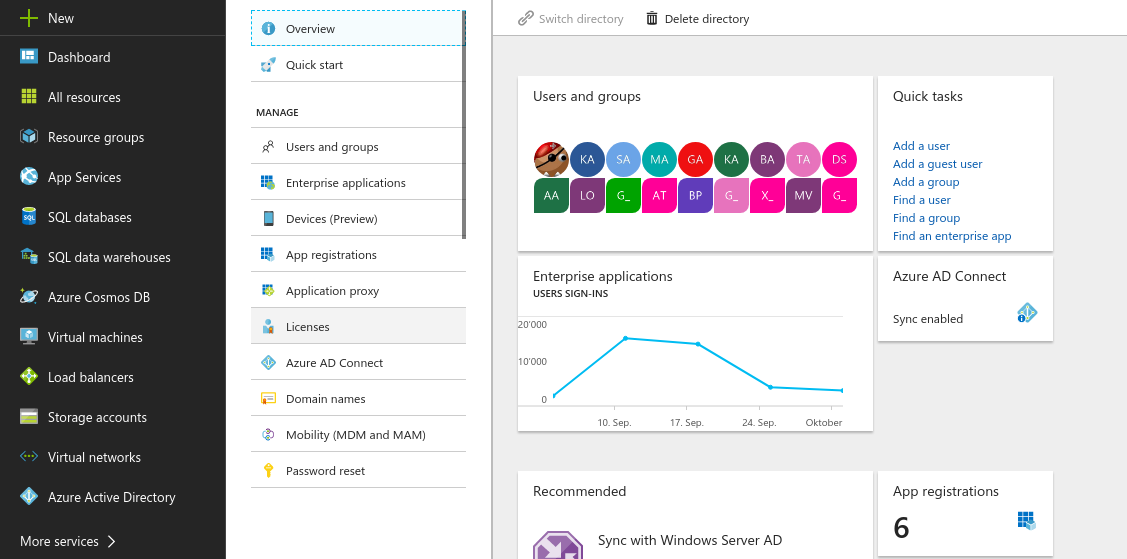
- Select Enterprise applications and create a new application. Choose to create a non-gallery application and give it a name
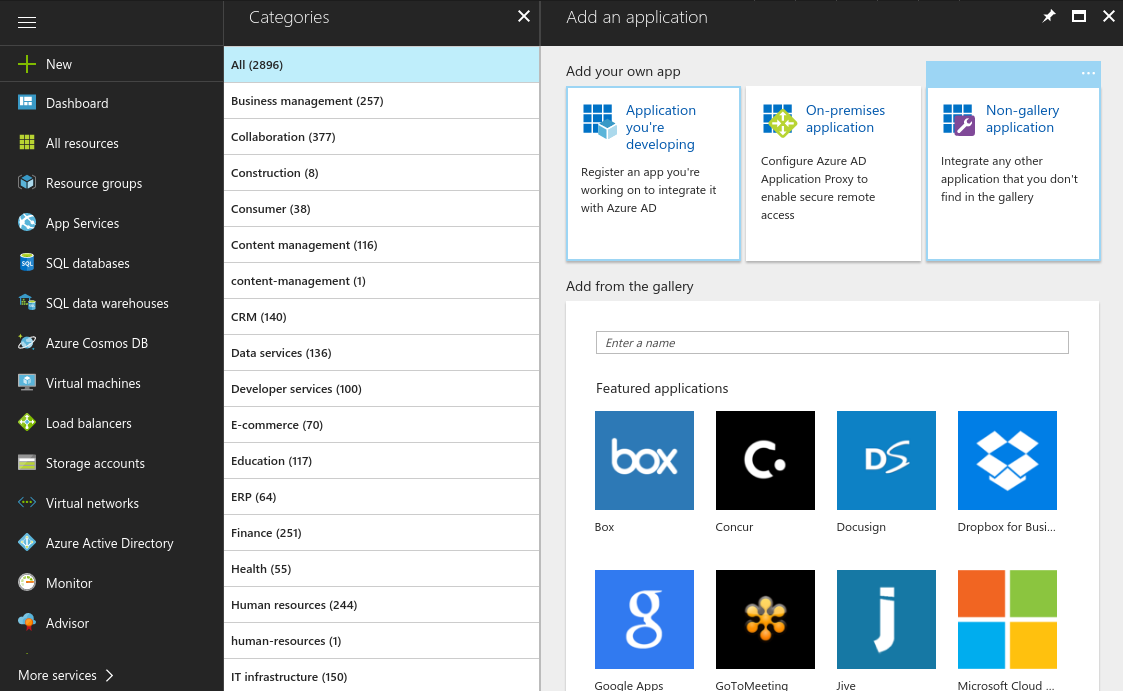
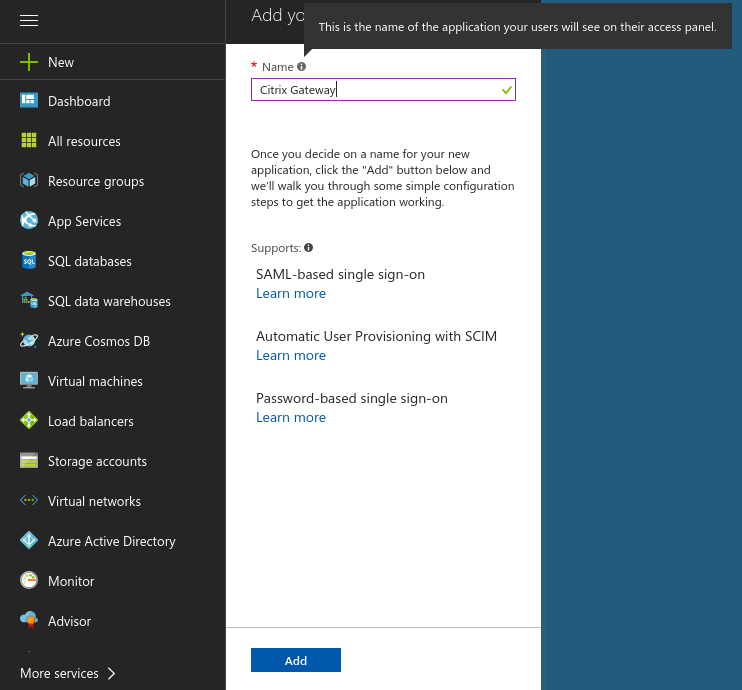
- After your enterprise application has successfully been created, you will see the Quick start panel.
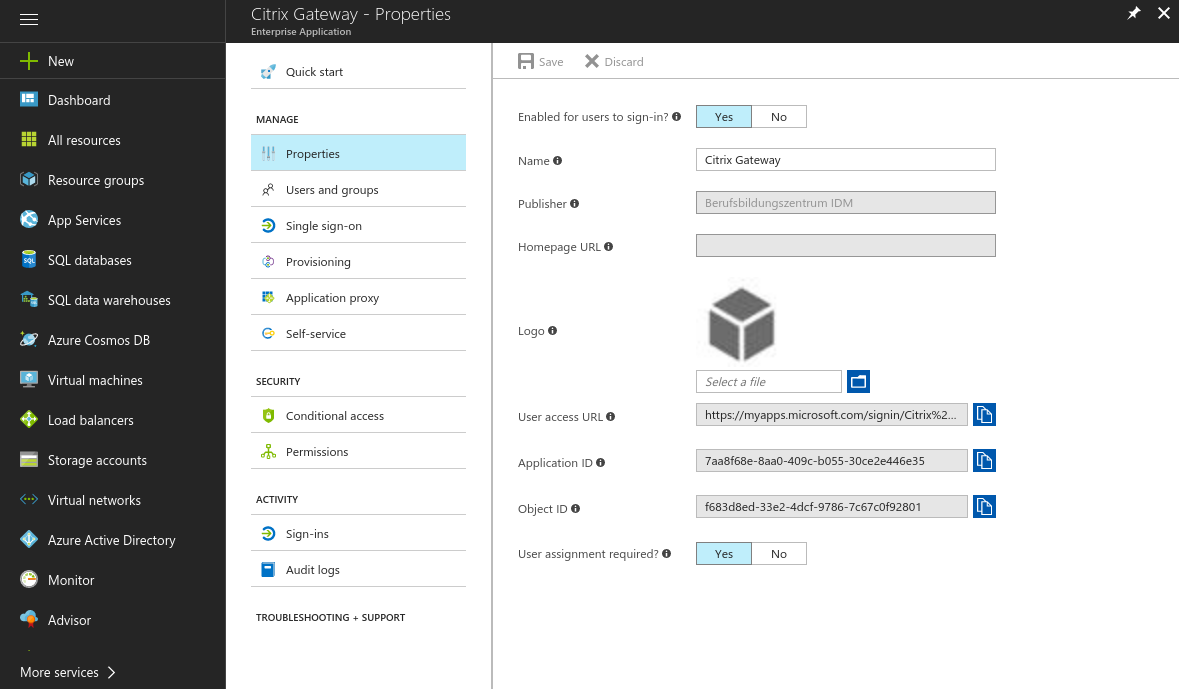
- In the properties of the enterprise app you may change the name of the application and assign a custom logo. Here you also can globally enable or disable the application and choose if a user assignment is required for the application. If this option is set to yes, users must first be assigned to this application before being able to access it. If this option is set to no, then any users who navigate to the application will be granted access.
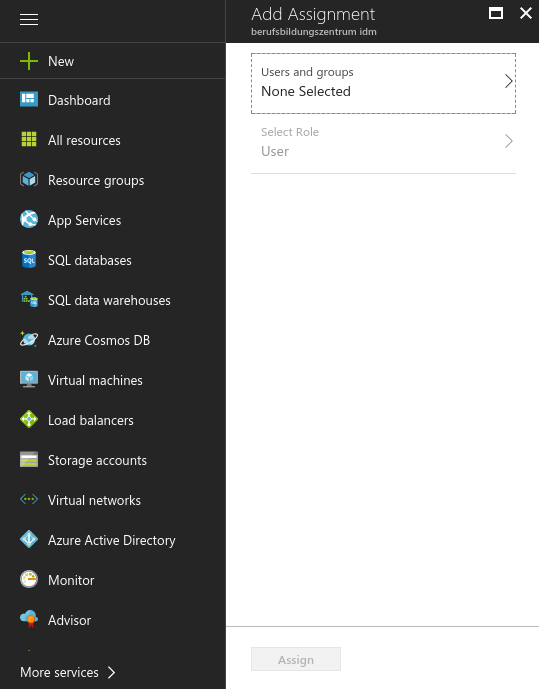
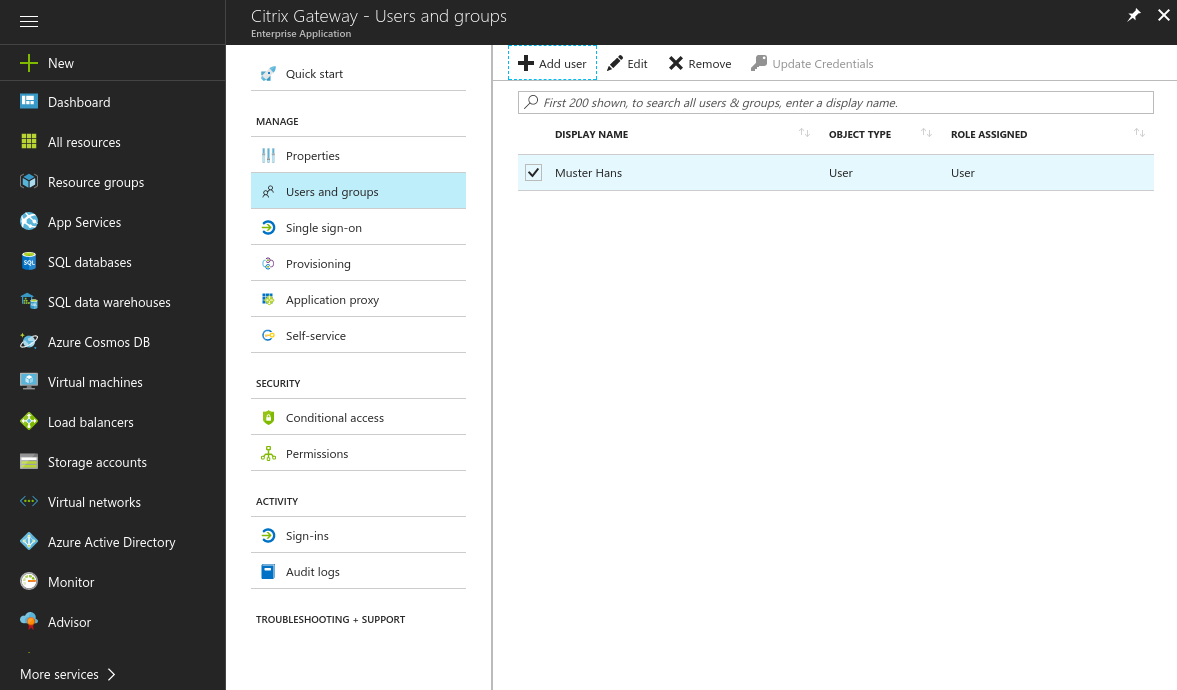
- Add users and groups you want to grant access to the application
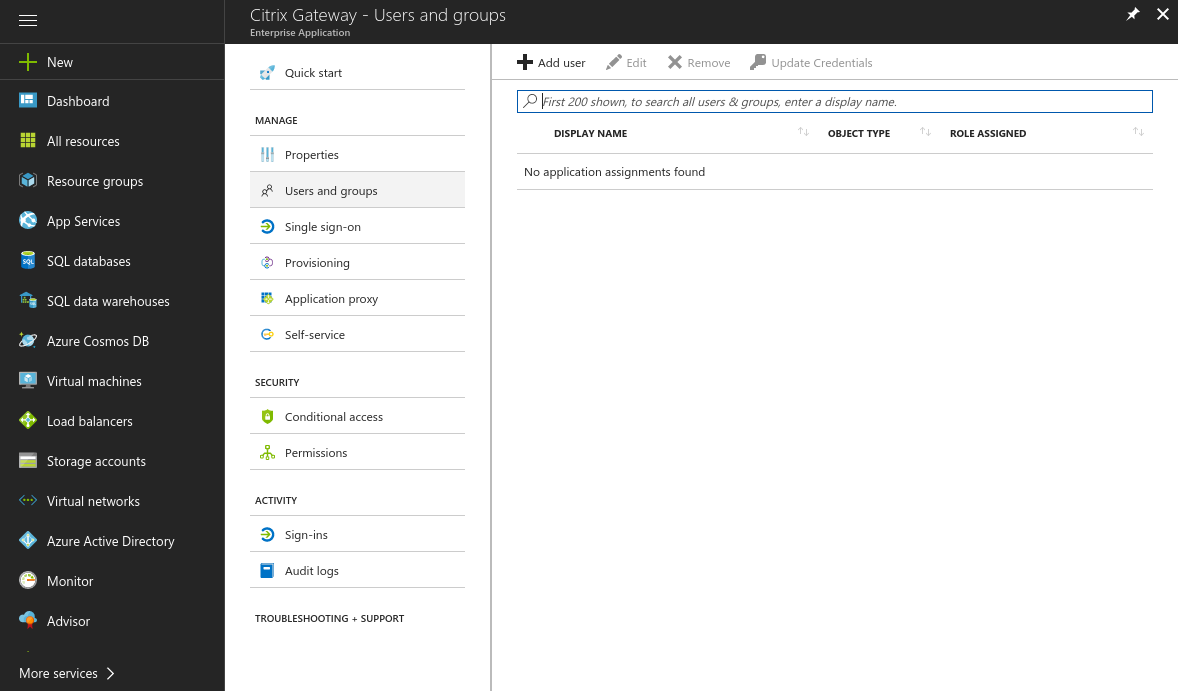
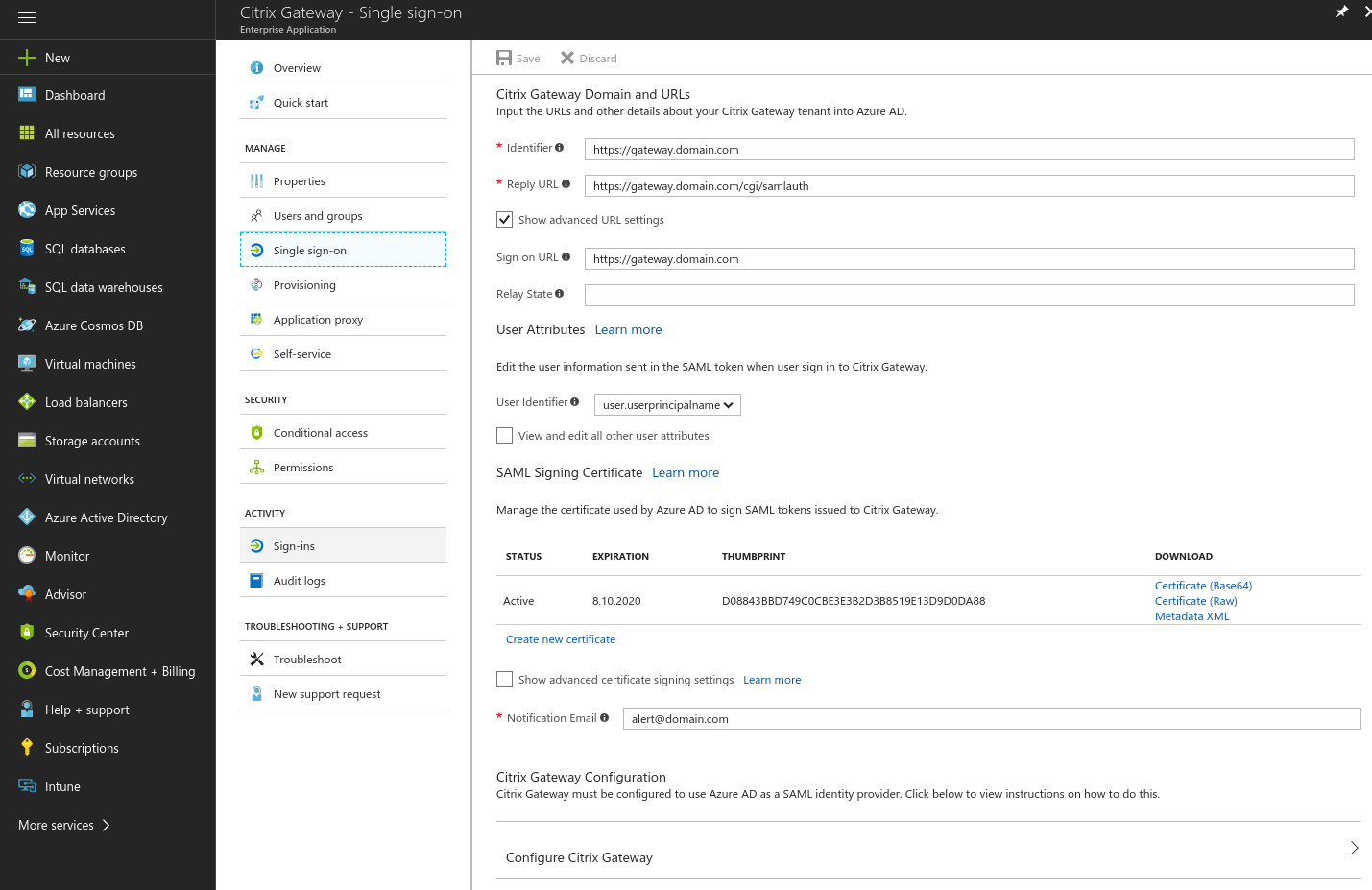
- Move on to the Single sign-on settings and enable SAML-based sign-on
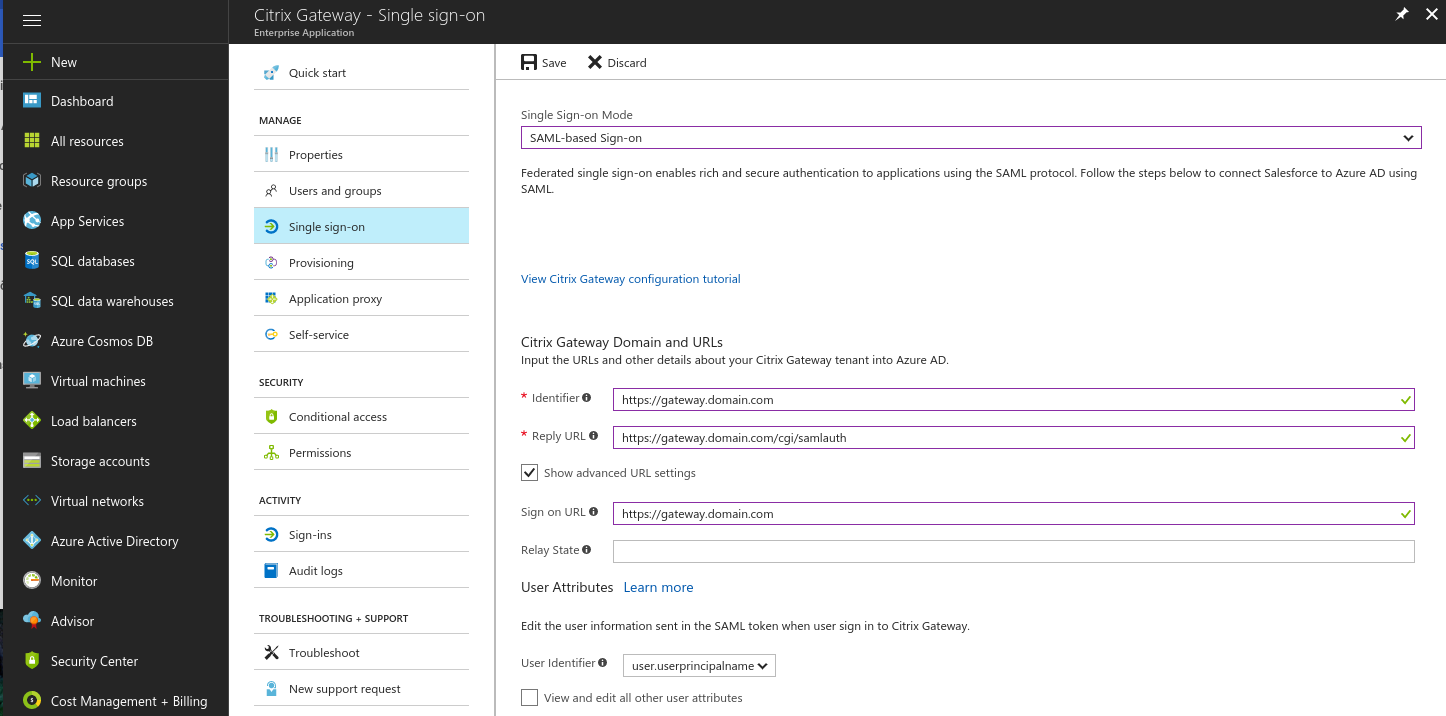
- Set the Identifier to the URL of your NetScaler gateway
- Set the Reply URL to the URL of your NetScaler gateway and append /cgi/samlauth
- Set the Sign on URL to your NetScaler gateway address
- Select user.userprincipalname for the User Identifier
- Make the new certificate active and set a notification email. When the active signing certificate approaches its expiration date, notifications are sent to this email address with instructions on how to update the certificate.
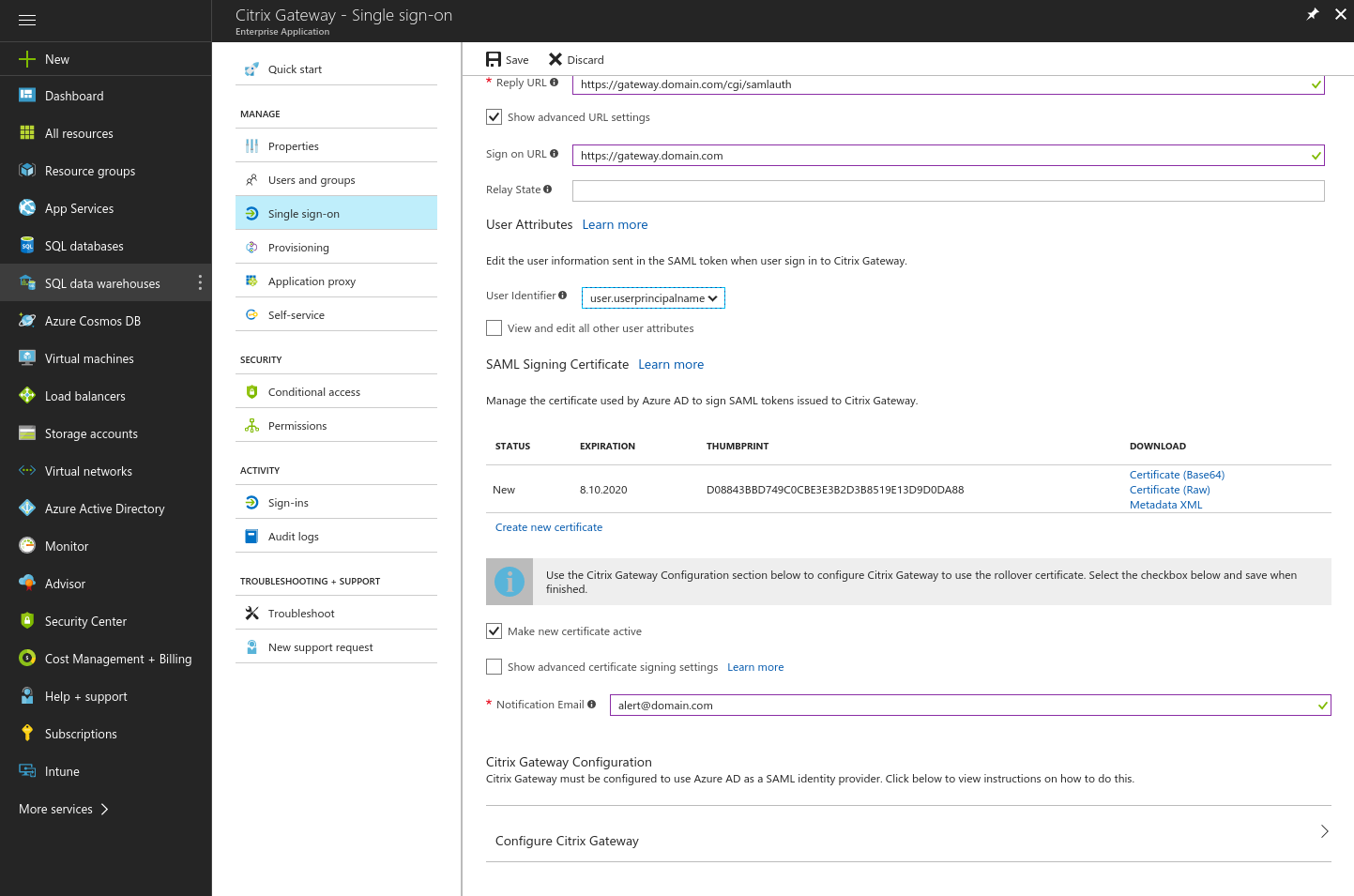
- Download the SAML signing certificate (Base64). We need this later on our NetScaler to set up the SAML authentication.
Citrix NetScaler Configuration
The configuration on the NetScaler side is quite straight forward. We just need to edit an existing virtual gateway to reflect our new SAML authentication against Azure AD.
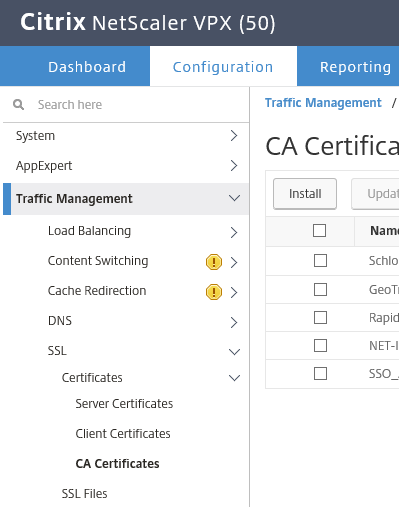
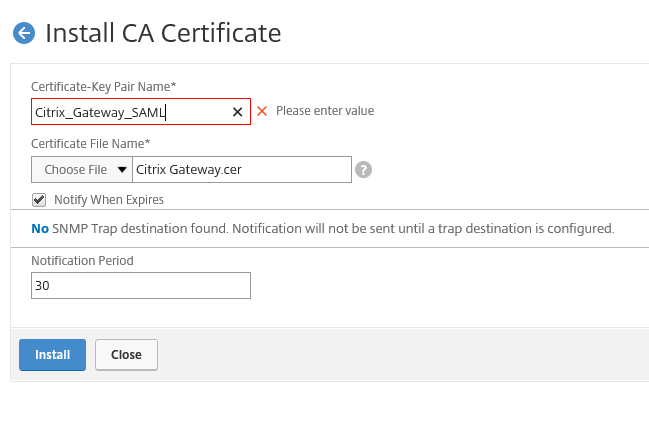
- Upload and install the SAML signing certificate to your NetScaler's CA certificates. This can be done under Traffic Management -> SSL -> Certificates -> CA Certificates.
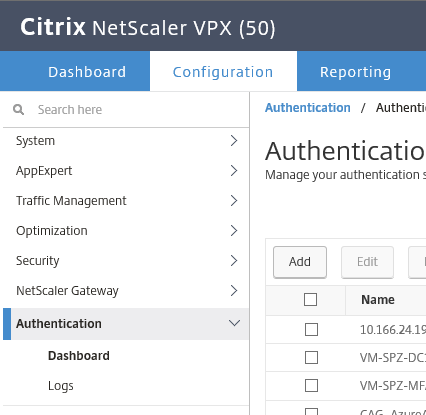
- Add the SAML authentication server via Authentication -> Dashboard
- Choose SAML for the server type and select the uploaded IDP certificate. For the signing certificate you may select your NetScaler server certificate. The Issuer Name has to match the Identifier you have set in your Azure enterprise app.
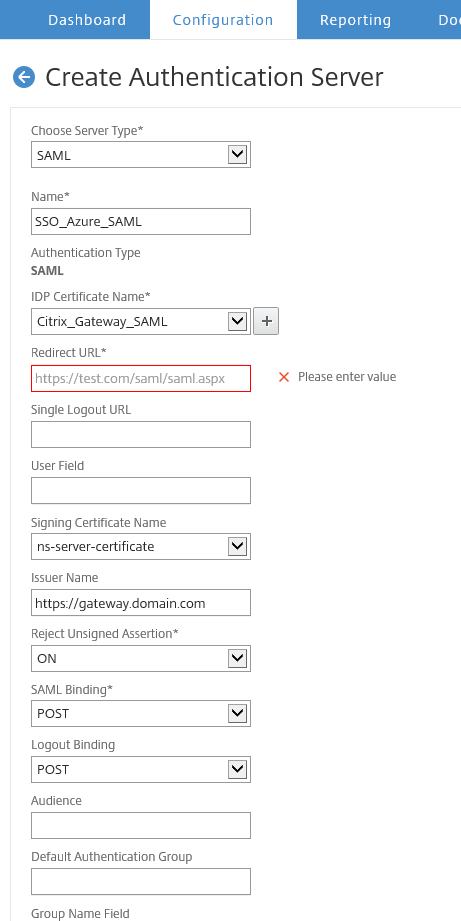
- Now you need to provide the Redirect URL and the Single Logout URL, which you can lookup in your enterprise app on Azure AD (Configure Citrix Gateway at the bottom of the page).
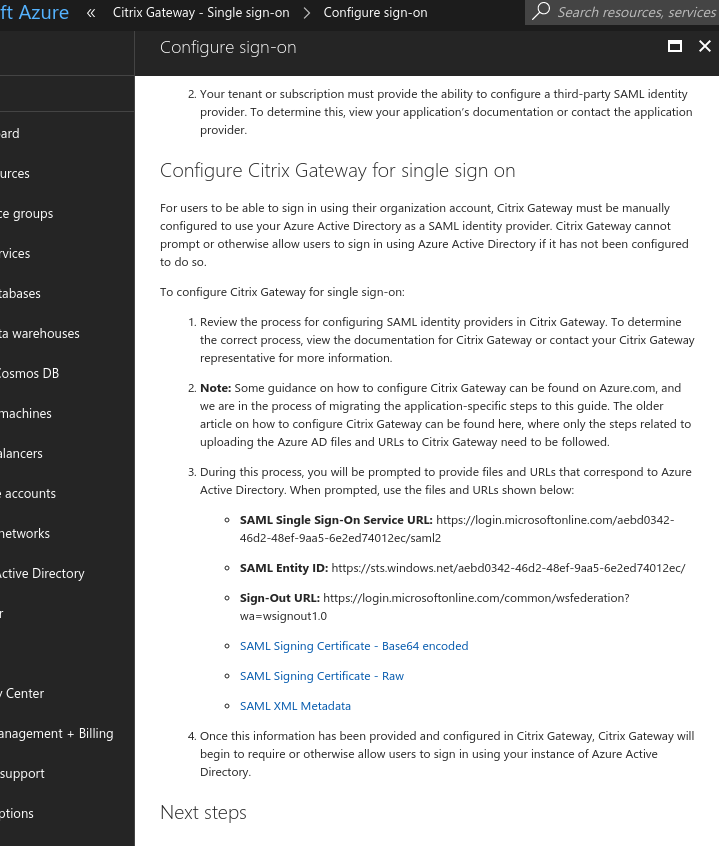
- Take note of the SAML Single Sign-On Service URL (Redirect URL) and the Sign-Out URL (Single Logout URL) and put the values in your authentication server configuration of the NetScaler.
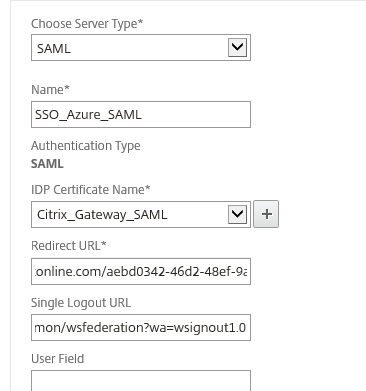
- As a last step before hitting create, set the Signature Algorithm and Digest Method to SHA256.
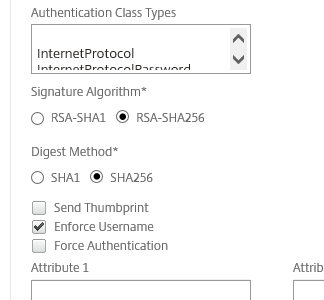
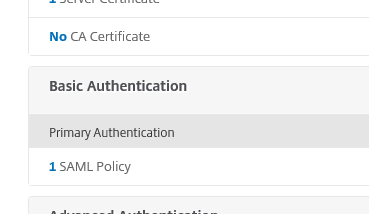
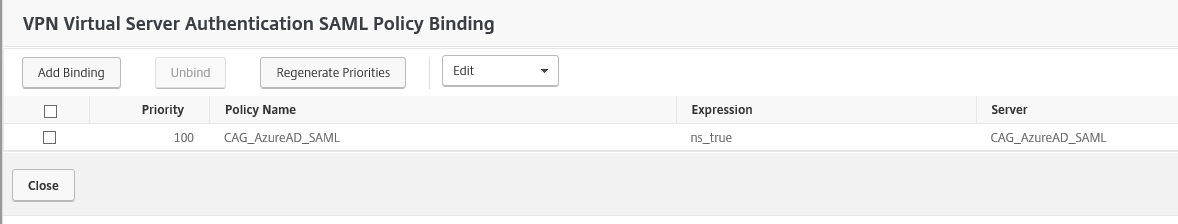
- Head over to your existing NetScaler Gateway Virtual Server configuration. Remove existing Active Directory authentication policies under Basic Authentication and replace them by creating a new SAML Policy for the Primary Authentication.
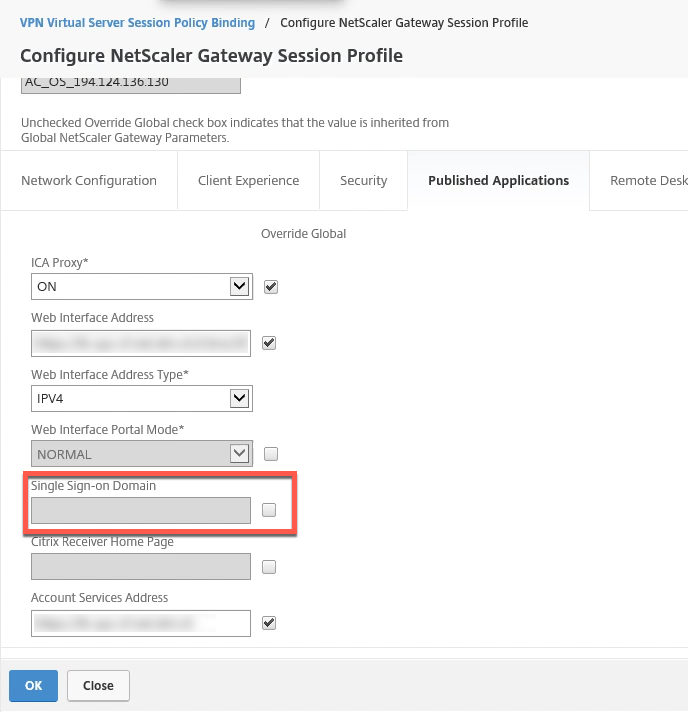
- Make sure to remove the Single Sign-on Domain from the Session Profile bound to the virtual server
Installation and setup of Citrix Federated Authentication Service
The next step is to implement Citrix Federated Authentication Service in your Citrix XenDesktop / XenApp environment. Without Citrix FAS your NetScaler SAML authentication will work, but your users would have to re-authenticate when starting desktops and apps from StoreFront, which is definitively not what you want since we aim to build a true Singe Sign-On solution for our users.
There is a great blog posts from awesome Citrix CTP Carl Stalhood on how to set up Citrix Federated Authentication Service. You find his detailed setup guide under http://www.carlstalhood.com/citrix-federated-authentication-service-saml/. It's a very straight forward process and I encourage you to follow his guide for the setup.
Citrix StoreFront Configuration
In a last step we need to enable Federated Authentication on your StoreFront servers and fully delegate credential validation to NetScaler Gateway. Enable Federated Authentication Service integration on StoreFront by running the following PowerShell commands: Get-Module "Citrix.StoreFront.*" -ListAvailable | Import-Module$StoreVirtualPath = "/Citrix/Store"
replace with your corresponding Store name!
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath$auth = Get-STFAuthenticationService -StoreService $storeSet-STFClaimsFactoryNames -AuthenticationService $auth -ClaimsFactoryName "FASClaimsFactory"Set-STFStoreLaunchOptions -StoreService $store -VdaLogonDataProvider "FASLogonDataProvider"
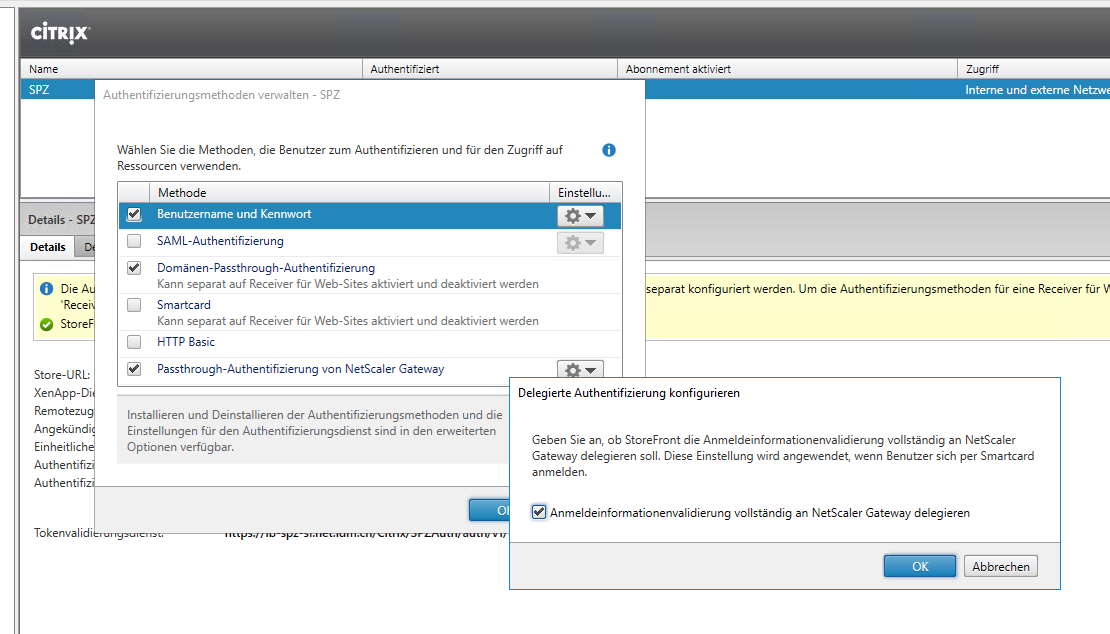
To delegate the credential validation to NetScaler Gateway, in the StoreFront management console go to Manage Authentication Methods of your Store, and select the settings of Pass-through from NetScaler Gateway, where you can enable Delegated Authentication.
Enabling and configuring Azure MFA for your Citrix Gateway enterprise app
That's it, you are almost done! The very last step is to enable and configure multi-factor authentication for your newly created Azure enterprise app.
- Create a new Conditional Access Policy
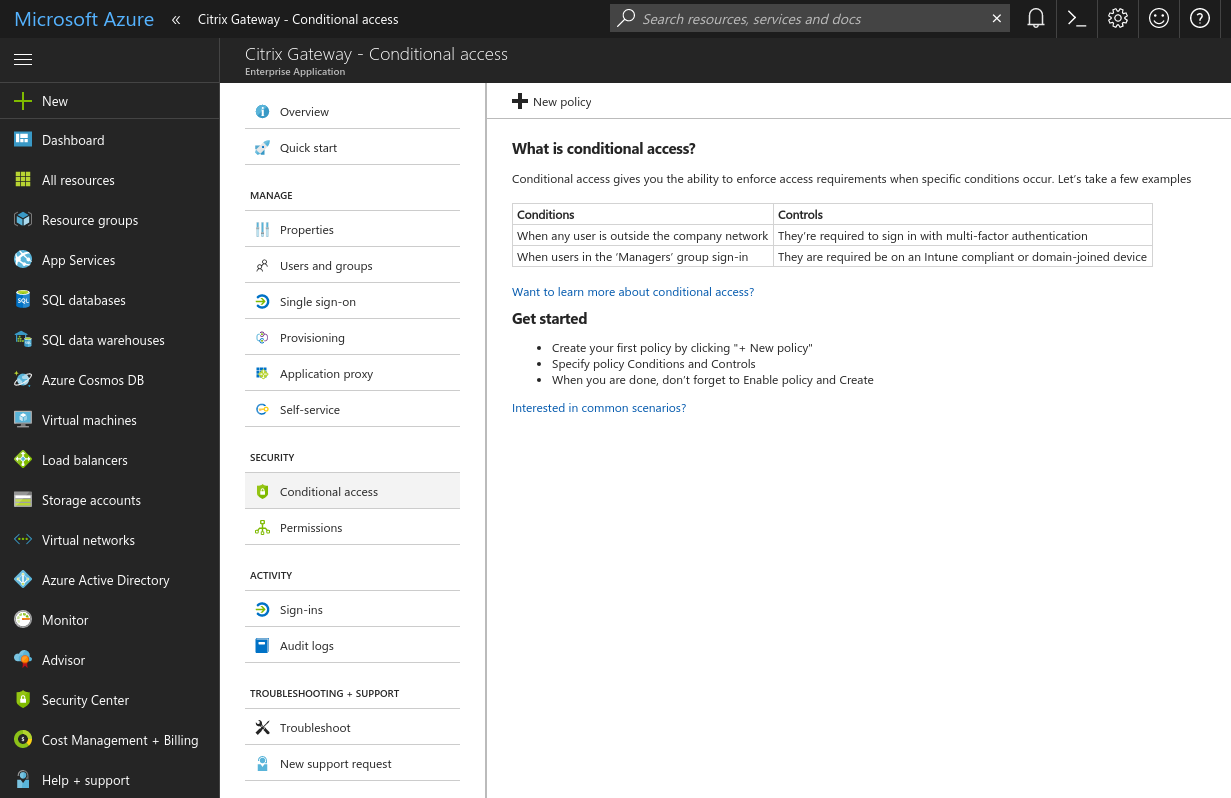
Create a new conditional access policy - Specify the users and groups to be included and / or excluded from the policy
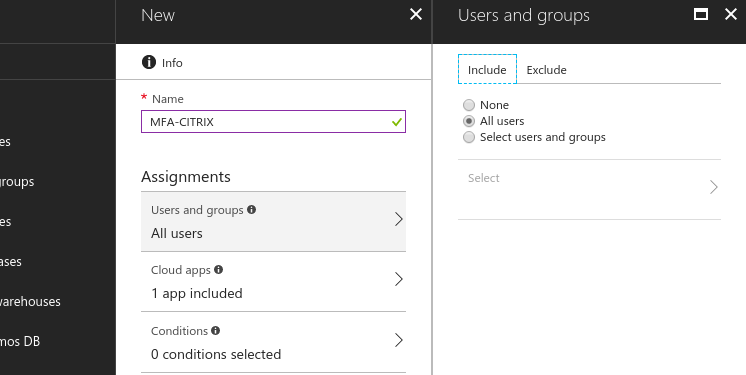
Users and groups in the directory that the policy applies to - Set the conditions which define when the policy will apply. You can specify conditions based on
- Device platforms (Android, iOS, Windows Phone, Windows, macOS)
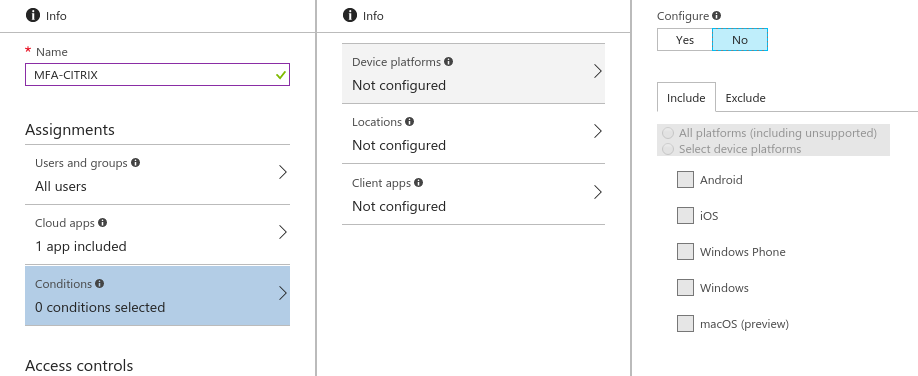
Platform the user is signing in from - Location (determined using IP address range the user is signing in from)
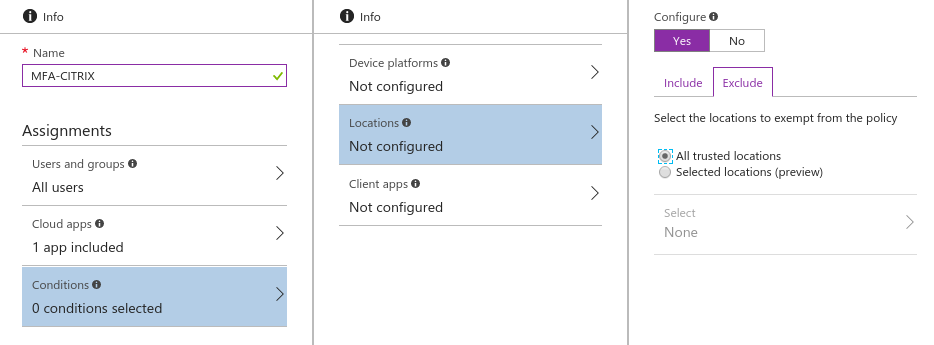
Location the user is signing in from
- Device platforms (Android, iOS, Windows Phone, Windows, macOS)
- Set Access Controls to block access or enforce additional requirements which need to be satisfied to allow access. You can enforce the following additional requirements
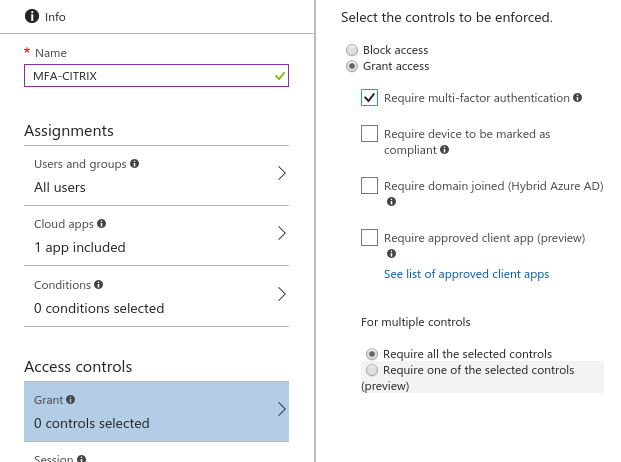
Select the controls to be enforced - Require multi-factor authentication - User must complete additional security requirements like phone call, text, authentication app challenge
- Require device to be marked as compliant - Device must be Intune compliant. If the device is non-compliant, the user will be prompted to bring the device under compliance
- Require domain joined (Hybrid Azure AD) - Devices must be Hybrid Azure AD joined
- Enable the Conditional Access Policy

Enable the Conditional Access Policy
Finally all done and you have implemented a highly user friendly way to provide your end-users with a secure remote access to your company's Citrix XenDesktop / XenApp environment.
See it in action in the following video clip and enjoy the outcome of your hard work!